

Right. I think the real vision isn’t that every single person self-hosts, but every community has somebody in it who does the self-hosting for the community. Everybody can be independent like villages instead of totally centralized like empires


Right. I think the real vision isn’t that every single person self-hosts, but every community has somebody in it who does the self-hosting for the community. Everybody can be independent like villages instead of totally centralized like empires

Ikea shelf instead of a rack, but I used metal shelves for better thermals!
Top to bottom:


I think it’s a great option to warn people about. Or even force switching of the keyboard for that one app. But it shouldn’t require you to set a system sitting.


It would be nice if people just said what they were thinking.
We wanted to juice our PSN subscriber numbers, so we’re forcing everybody to make a PSN account, so hopefully they spend more money with us in the future


they said it had widgets in the announcement blot


I have seen the tuta news… That really did annoy me, I emailed them every time I get one of them asking them not to do it anymore. It should just be a regular email. Not some special fake email.


I don’t see any ads


The general topic was about self-hosting. IPv6 is very useful for self-hosting,… connections.
I’ll admit there is a critical mass problem with torrenting clients, but if you’re trying to set up a wire guard tunnel with your friends, IPv6 is a absolute banger


In most environments ipv6 bypasses cgnat (because, why would you need a nat with ipv6).


I myself have no life and must grow the factory.
Just lost nuclear power on gleba because the nuke shuttle got stuck…
The Penta pests will destroy the gleba outpost.mm again unless it’s fixed asap. Can’t stop!


I don’t believe it requires a Google account.
I just used it on grapheneos, it does recommend you use a separate Google account for the private space, but I don’t have Google account on the phone, I was able to create a private space without any issue.
This feels very much like a second profile, like a workspace. So now you can have three profiles on your main phone login. Normal, private, work.
That’s nice. I would have liked it if the lock button wasn’t there, better to not reveal it at all… Upon checking the settings, there is a hide option. So yeah this is great
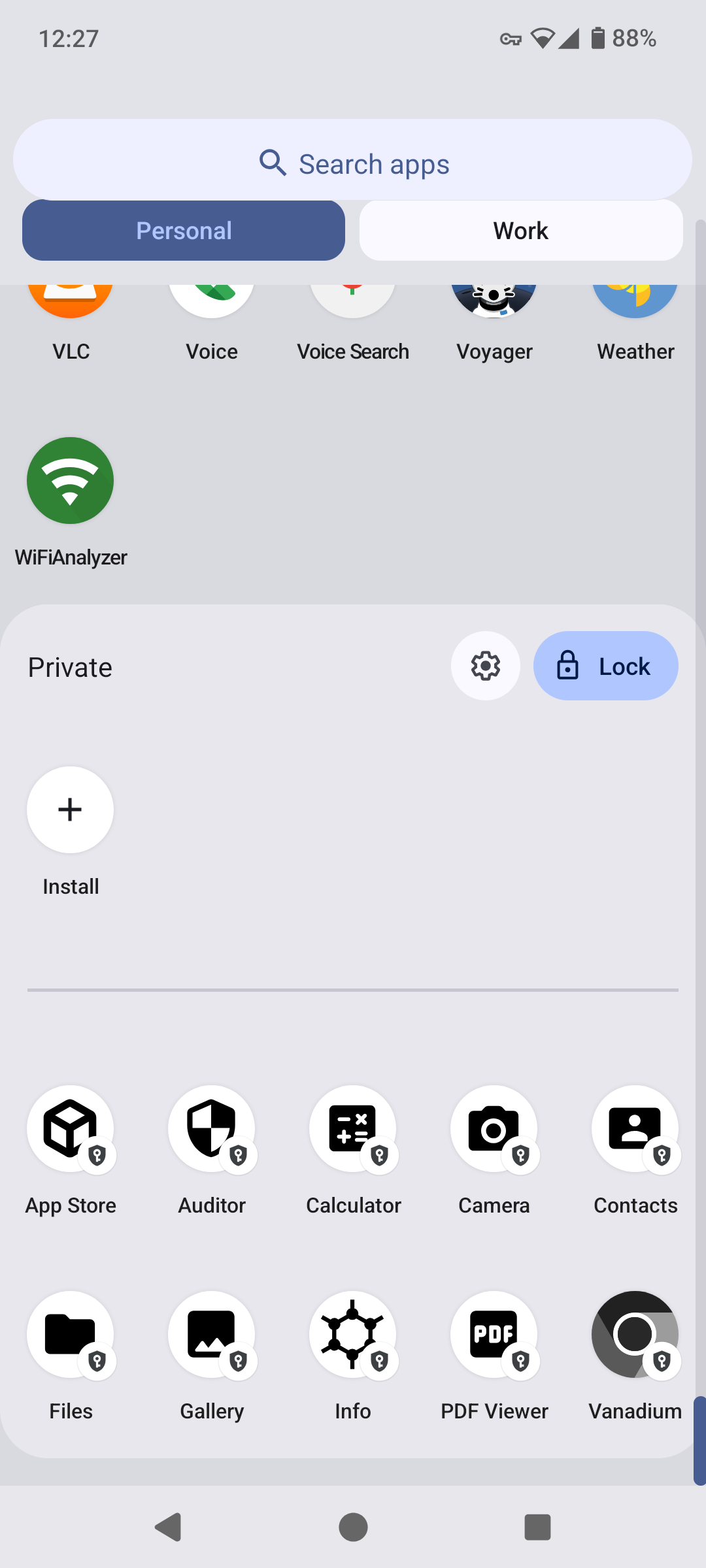
I hid my private space, and now I can’t unhide it. I have to go through settings to show it again. Supposedly you should be able to open it by searching for “private space”. Might be a GOS bug.
This is perfect for banking apps, password managers, anything that you don’t need to get notifications from


https://www.wireguard.com/netns/
Here is a good how to for wireguard. Most commercial VPNs let you connect directly with wireguard.
Basically crate the interface in your clearnet namespace and then move it to your vpn namespace


That game is such a vibe done perfectly


To be fair, the devs know not everybody can afford it, there’s zero piracy protection in the game. You can copy the game from somebody steam install, play it locally no problems, play it off the network, even play on multiplayer servers that have turned off user verification. It’s the perfect lan party game.
https://steamdb.info/app/645390/
On steam, at least, there is regional pricing. The lowest current price is $7
https://github.com/evanman83/OURS-project
I know it’s boxy, but it’s totally open source, you could slap a small screen in there and then figure out how to jigsaw the rest of the pieces into a smaller form factor!!
Oh God. The spaghetti belt puzzles. That’s a dark art, so tantalizing, but sets traps for the future.
Like having one speed belt, and then a different speed belt going below it. Works for the moment, great throughput, as soon as an upgrade planner is applied boom everything stops working. A little time bomb for your future self


I wish it were that easy, there’s a lot of shared architecture in CPU design. So maybe there’s cache lines that are shared, those have to be disabled.
Architecturally, maybe memory tagging for cash lines that in addition to looking at the TLB and physical addresses also looks at memory spaces. So if you’re addressing something that’s in the cache Even for another complete processor, you have to take the full hit going out to main memory.
But even then it’s not perfect, because if you’re invalidating the cache of another core there is going to be some memory penalty, probably infotesimal compared to going to main memory, but it might be measurable. I’m almost certain it would be measurable. So still a side channel attack
One mitigation that does come to mind, is running each program in a virtual machine, that way it’s guaranteed to have completely different physical address space. This is really heavy-handed, and I have seen some papers about the side channel attacks getting leaked information from co guest VMs in AWS. But it certainly reduces the risk surface
And if you’re one of the people who can crack a beer open with the owners of Google, then you found your right community.
However, in the general case, I don’t think these count as any individuals communities. You can’t rub elbows with the people maintaining Google and Facebook. You can’t talk to them about issues you’re having, they’re not going to dynamically modify the system for special cases that are important to your community. A community is a group of people who know each other.